Penetration Testing Models
There are two major models for conducting a network penetration testing. The first is a ‘cyber threat model’ in which the tester simulates the behavior of an insider. This means that the tester will ask employees for access privileges, and he will then use those credentials to infiltrate data. The second is an ‘access privileges’ model, which involves testing the security of authentication and Data Loss Protection protocols.
This approach is best implemented through social engineering. By conducting social media research, you can identify important employees at your organization. Then, create phishing emails that mimic emails from human resources. These emails will ask recipients to download a file intended for HR purposes. This attachment will be embedded with Key Logger or Rootkit malware. Once inside the organization, the malicious code will start to work. If your employees click on this link, they’ll be able to access sensitive data, which can lead to a security breach.
Once the network is set up, the next step is to identify any vulnerabilities. This process generally starts with automated scanning, but quickly evolves into manual testing. The most important step in this process is the reporting phase. A comprehensive report is needed for your organization to learn what the findings were, and implement them to protect the organization. However, the first step of this process is to identify the risks of each asset. In some cases, this information will be sensitive or contain trade secrets.
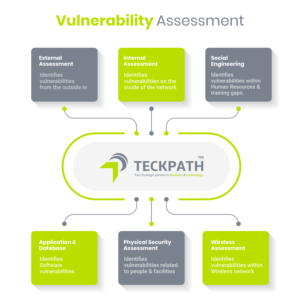
Network Penetration Testing Models
Another model for performing network penetration tests is to find vulnerabilities in security protocols. For example, businesses can use weak encryption protocols, such as WPA2, which has recently been exposed by Belgian cyber researchers. The testing will uncover system components and misconfigurations. This will help businesses protect their networks from hackers. There are several other types of networks, and a good provider can apply both types in a network penetration test. This type of testing can give you valuable insight into your business’s security posture and empower you to fix them.
The second step in a penetration test is the mapping out of vulnerabilities. During the reconnaissance phase, attackers will attempt to use security flaws discovered in the network to access sensitive data. The test is not effective unless the vulnerabilities are documented. It is critical that your company performs network penetration tests and documents the results. These results will help you make more informed decisions about security. After all, the goal of penetration testing is to protect your business, so your customers are secure.
Network penetration tests are generally conducted with the help of internationally recognized frameworks. The underlying framework of network penetration tests is based on the Penetration Testing Execution Standard (PTES).

